| 知乎专栏 |
https://github.com/gaomd/docker-ikev2-vpn-server
启动 VPN Server
docker run --privileged -d --name ikev2-vpn-server --restart=always -p 500:500/udp -p 4500:4500/udp gaomd/ikev2-vpn-server:0.3.0
复制配置文件,并将配置文件 ikev2-vpn.mobileconfig 发送给客户端
docker run --privileged -i -t --rm --volumes-from ikev2-vpn-server -e "HOST=vpn1.example.com" gaomd/ikev2-vpn-server:0.3.0 generate-mobileconfig > ikev2-vpn.mobileconfig docker run --privileged -i -t --rm --volumes-from ikev2-vpn-server -e "HOST=8.219.81.14" gaomd/ikev2-vpn-server:0.3.0 generate-mobileconfig > ikev2-vpn.mobileconfig
http://www.strongswan.org/
User -> Windows 10 Desktop -> Inside Greatwall -> VPN Server(Hongkong/Other) -> Outside Greatwall
首先在海外部署一台服务器,将服务器配置成为VPN服务器,然后桌面用户通过该服务器,你懂的......
由于pptp,l2tp,openvpn 先后被墙,所以我选择了IKEv2。
CentOS 7 环境
yum install -y strongswane yum install -y haveged systemctl enable haveged systemctl start haveged cd /etc/strongswan
创建自签名CA根证书
# 私钥证书 strongswan pki --gen --type rsa --size 4096 --outform der > ipsec.d/private/CARootKey.der chmod 600 ipsec.d/private/CARootKey.der # 公钥证书 strongswan pki --self --ca --lifetime 3650 --in ipsec.d/private/CARootKey.der --type rsa --dn "C=NL, O=Example Company, CN=StrongSwan Root CA" --outform der > ipsec.d/cacerts/CARootCert.der strongswan pki --print --in ipsec.d/cacerts/CARootCert.der
颁发服务器证书
# 私钥证书 strongswan pki --gen --type rsa --size 2048 --outform der > ipsec.d/private/ServerKey.der chmod 600 ipsec.d/private/ServerKey.der # 公钥证书 strongswan pki --pub --in ipsec.d/private/ServerKey.der --type rsa | strongswan pki --issue --lifetime 730 --cacert ipsec.d/cacerts/CARootCert.der --cakey ipsec.d/private/CARootKey.der --dn "C=NL, O=Example Company, CN=vpn.example.org" --san vpn.example.com --san vpn.example.net --san 147.90.44.87 --san @147.90.44.87 --flag serverAuth --flag ikeIntermediate --outform der > ipsec.d/certs/ServerCert.der strongswan pki --print --in ipsec.d/certs/ServerCert.der
颁发客户端用户证书
# 私钥证书 cd /etc/strongswan/ strongswan pki --gen --type rsa --size 2048 --outform der > ipsec.d/private/ClientKey.der chmod 600 ipsec.d/private/ClientKey.der # 公钥证书 strongswan pki --pub --in ipsec.d/private/ClientKey.der --type rsa | strongswan pki --issue --lifetime 730 --cacert ipsec.d/cacerts/CARootCert.der --cakey ipsec.d/private/CARootKey.der --dn "C=NL, O=Example Company, CN=netkiller@msn.com" --san "netkiller@msn.com" --san "neo.chan@live.com" --outform der > ipsec.d/certs/ClientCert.der # 证书转换,转过过程是 der -> pem -> p12 openssl rsa -inform DER -in ipsec.d/private/ClientKey.der -out ipsec.d/private/ClientKey.pem -outform PEM openssl x509 -inform DER -in ipsec.d/certs/ClientCert.der -out ipsec.d/certs/ClientCert.pem -outform PEM openssl x509 -inform DER -in ipsec.d/cacerts/CARootCert.der -out ipsec.d/cacerts/CARootCert.pem -outform PEM # 请为证书设置一个密码 openssl pkcs12 -export -inkey ipsec.d/private/ClientKey.pem -in ipsec.d/certs/ClientCert.pem -name "Client's VPN Certificate" -certfile ipsec.d/cacerts/CARootCert.pem -caname "strongSwan Root CA" -out Client.p12 </screen> <para>p12中包含了CA证书,客户端私钥证书,客户端公钥证书。Client.p12 发送给最终用户即可</para> <tip> <para>如果你安装过 OpenVPN 那么会很好理解,上述的几个步骤等同于:</para> <screen><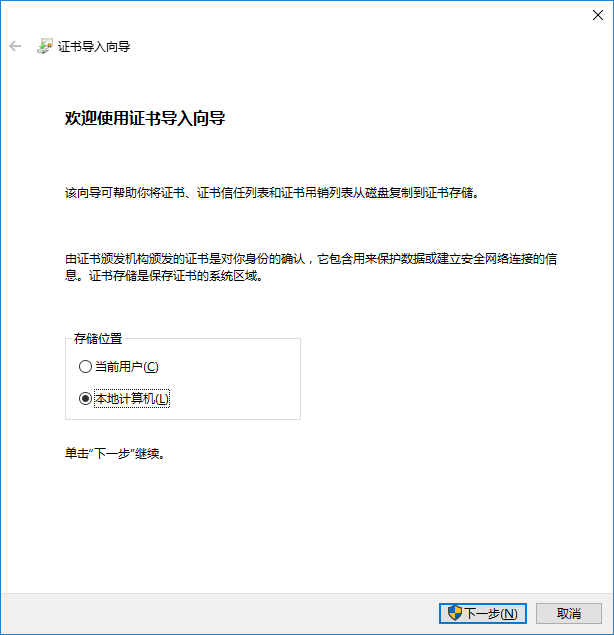 |
选择“本地计算机”
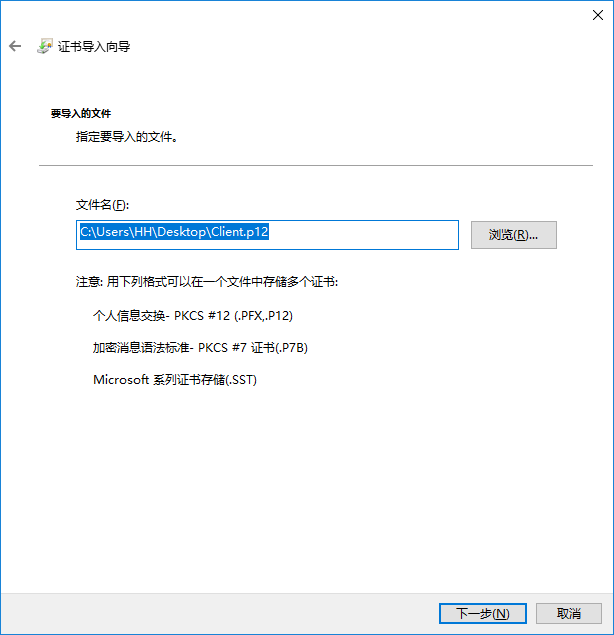 |
下一步
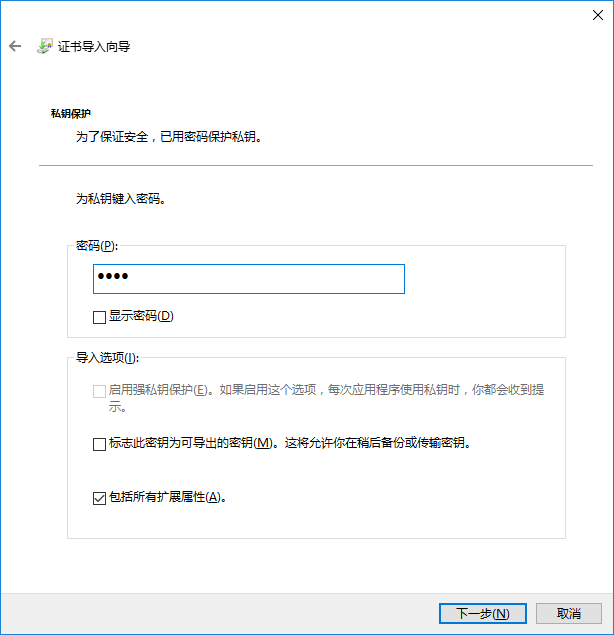 |
输入证书密码,下一步
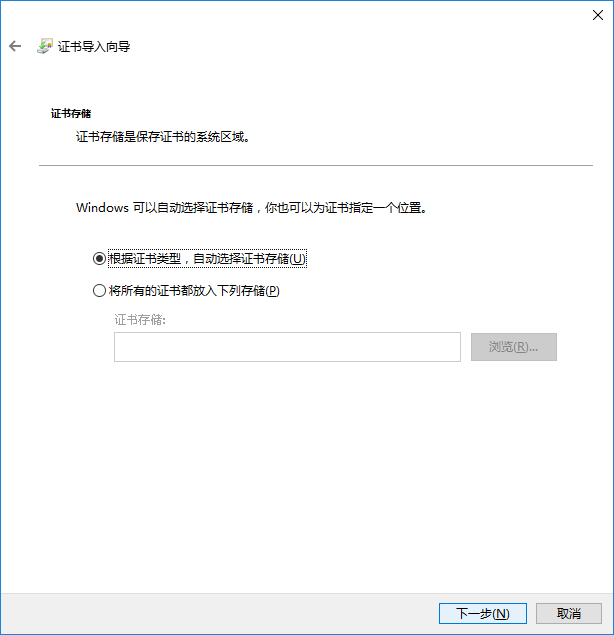 |
下一步
 |
点击“完成”按钮
 |
证书导入成功
接下来配置 Windows 10 VPN 链接
任务条最右测系统托盘区,点击网络图标,再点击“网络设置”
 |
点击“VPN”,然后点击“添加 VPN 链接”
 |
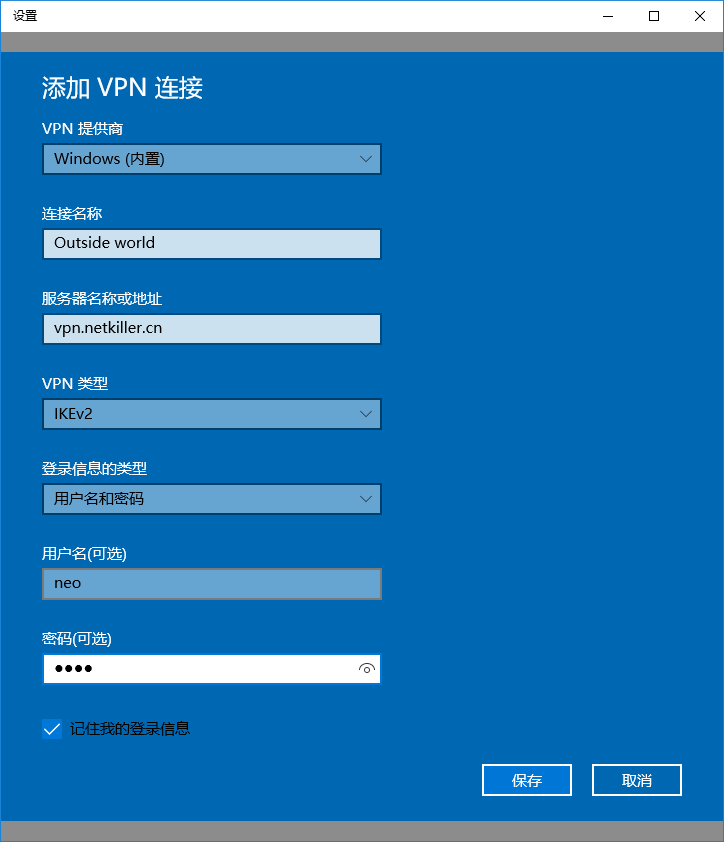
填写信息并保存
 |
点击“更改适配器选项”
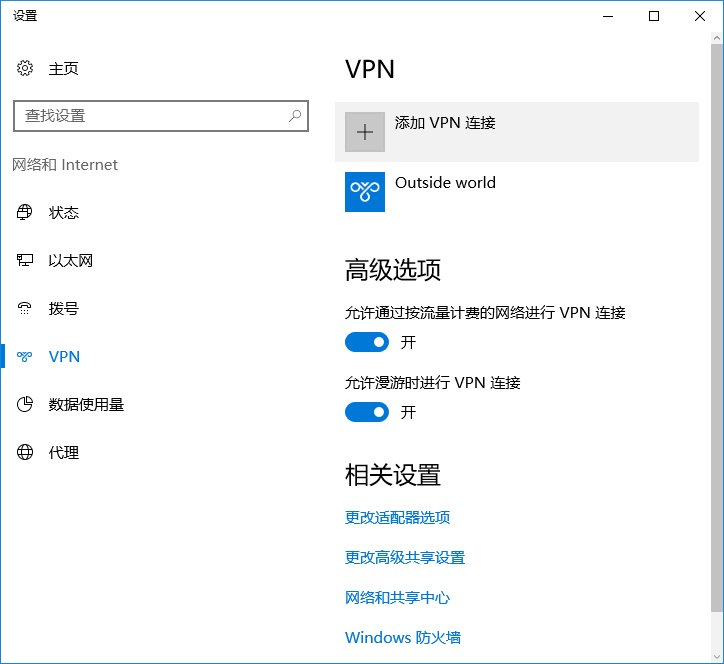 |
找到VPN网络适配器,鼠标右键点击,选择“属性”
 |
 |
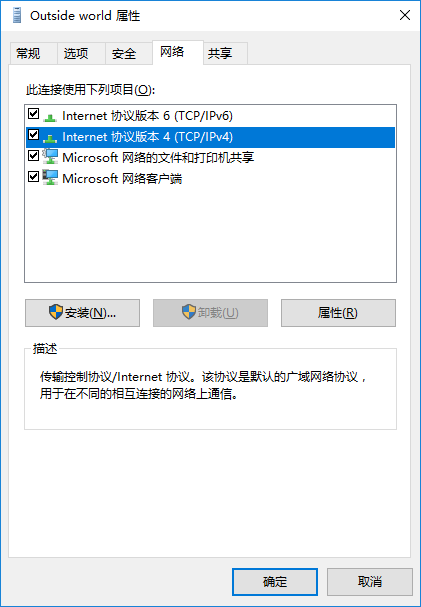
切换到“网络”选项卡,选中“IPv4”后点击“属性按钮”
 |
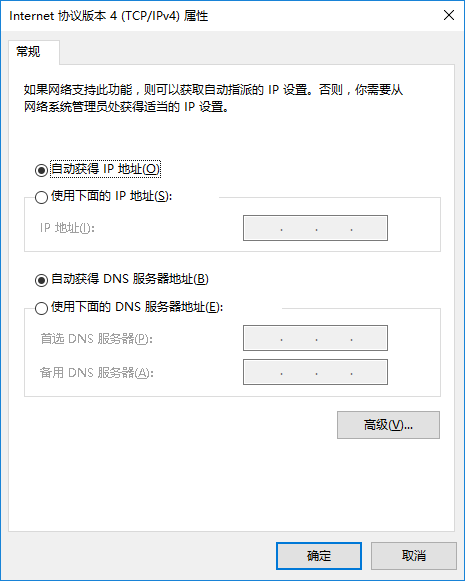
点击“高级”按钮
 |
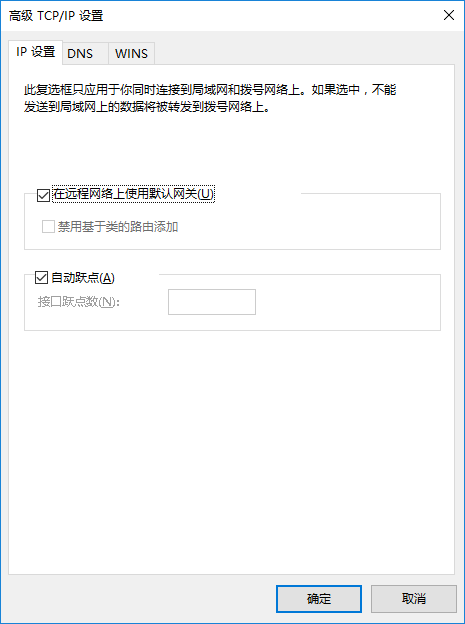
勾选“在远程网络上使用默认网关”,然后点击“确定”按钮
 |
回到网络设置界面,点击VPN图标,再点击链接
 |
现在查看你的IP地址,正确应该是经过VPN Server 访问互联网。